Adding security to a data set
To apply security to a data set, select Security, then specify the security IDs in Access Control List Expression.
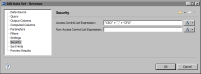
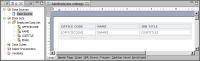
Figure 20‑11 shows an example where the expression specified for the data set’s Access Control List Expression property is:
"CEO" + "," + "CFO"
Figure 20‑11 Data security applied to the data set
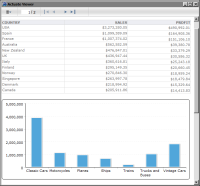
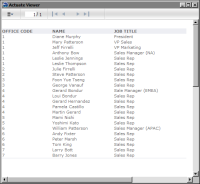
In the example, only users with the CEO or CFO role can access the data set. For example, in a report that contains a table that uses the secured data set, only the CEO and CFO can view the data in the table, as shown in
Figure 20‑12. Other users see an empty table, as shown in
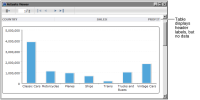
Figure 20‑13.
Figure 20‑12 Preview of the report for the CEO and CFO roles
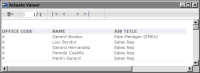
As
Figure 20‑13 shows, the table does not display data from the secured data set, but the labels in the table’s header appear. To hide the entire table if there is no data, use the table’s Visibility property. Specify an expression, as shown in the following example, as the condition for hiding the table. In the expression, Row_Count is a column binding that uses the COUNT function to return the number of rows in the table.
row["Row_Count"] == null
Figure 20‑13 Preview of the report for roles other than CEO or CFO
You can also apply security to rows in a data set, which is a typical approach. To do so, specify the security IDs in Row Access Control List Expression.
Figure 20‑14 shows an example where the expression specified for the Row Access Control List Expression property is:
"HR Director" + "," + "Manager: Office " + row["OFFICECODE"]
Figure 20‑14 Data security applied to data set rows
Security applied to data set rows acts as a filter. In the example shown in
Figure 20‑14, the HR Director can view all rows in the data set. Managers can view only rows that pertain to their department as specified by the office code.
Figure 20‑15 shows a report design that uses the secured data object. In the design, a table contains data elements that access the data set columns in the data object.
Figure 20‑15 Report design that uses data from a data set in a secured data object
When run and viewed by the HR Director, the report displays all the rows in the data set, as shown in
Figure 20‑16.
Figure 20‑16 Preview of the report for the HR Director role
When run and viewed by the manager of a specific office code, the report displays only the rows for that office.
Figure 20‑17 shows the report thatManager: Office 4 sees.
Figure 20‑17 Preview of the report for the Manager: Office 4 role
As the example shows, applying security to data set rows is useful for creating a single data set that provides different data to different users.
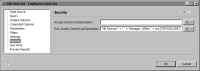
You can also apply security to each column in a data set. For example, you can restrict a profit/loss column or a salary column to users with executive‑level roles. To do so, select Output Columns, select the column, then specify the security IDs in Access Control List Expression.
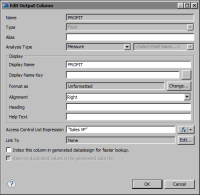
Figure 20‑18 shows an example where the expression specified for a column’s Access Control List Expression property is:
"Sales VP"
Figure 20‑18 Data security applied to a column in a data set
In the example, only users with the Sales VP role can access data in the PROFIT column.
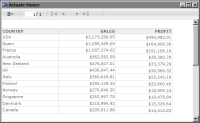
Figure 20‑19 shows a report using the PROFIT column and how the report appears to a user with the Sales VP role.
Figure 20‑19 Preview of the report for the Sales VP role
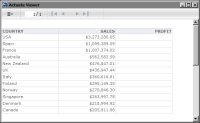
Figure 20‑20 shows the same report, but as viewed by a user without the Sales VP role. There is no data in the PROFIT column; only the PROFIT label appears in the table header. To hide the entire column if there is no data, set the column’s Visibility property to an expression, such as the following:
row["PROFIT"] == null
Figure 20‑20 Preview of the report for roles other than Sales VP
Security at the column level also controls the availability of certain columns to users designing a dashboard in BIRT 360 or a report in BIRT Studio.