Installing a Java RSSE application
A single SOAP-based RSSE application provides the security implementation for an entire iHub cluster. The RSSE application runs as a web service in the BIRT iHub servlet container.
The default location for an RSSE web service application is $SERVER_HOME/web/webapps/acrsse. This location must be accessible to all nodes in the cluster.
How to install a Java RSSE application
Install a Java RSSE application to run on BIRT iHub by performing the following tasks:
1 Make a copy of the $SERVER_HOME/web/webapps/acrsse directory. For example, copy the directory to the following location:
$SERVER_HOME/web/webapps/myacrsse
2 Copy the application archive file to the lib directory of the BIRT iHub servlet container in the following location:
$SERVER_HOME/web/webapps/myacrsse/WEB-INF/lib
3 Extract the file, class.properties, from the application archive file, to the following location:
$SERVER_HOME /web/webapps/myacrsse/WEB-INF/classes/com/actuate11/rsse/wsdl
If necessary, create the subdirectories, /com/actuate11/rsse/wsdl, manually or use the archive extraction tool to create the subdirectories when extracting the class.properties file.
4 Using a source code editor, open the class.properties file and change its single line of code to reference the main class of the application in the archive file:
class=com.actuate11.rsse.mySampleApp.SampleRSSE
Configuring and deploying an LDAP configuration file
To use a Java RSSE sample application that utilizes LDAP for external user authentication or registration, configure and deploy an LDAP configuration file to the BIRT iHub etc directory before enabling the web service on the Encyclopedia volume.
How to configure and deploy an LDAP configuration file for external authentication
To configure and deploy the LDAP configuration file for external authentication perform the following operations:
1 Using a source code editor, create the LDAP configuration file by typing the following code, substituting the values appropriate for the LDAP server installation such as:

Name of the LDAP server

Port number where the LDAP server listens

UserBaseDN, including the attributes for the organizational unit, ou, and domain components, dc
<!-- ldapconfig_$volumeName.xml -->
<!--"-->
<Config>
<!--The name of the LDAP server.--> <Server>servername.actuate.com</Server>
<!--The port number where the LDAP server listens.-->
<Port>389</Port>
<!--The base DN used for user queries.-->
<UserBaseDN>ou=actuate users, dc=actuate, dc=com
</UserBaseDN>
</Config>
2 Save the file to the following location, naming the file, ldapconfig_$volumeName.xml, changing $volumeName to the Encyclopedia volume name:
$SERVER_HOME\etc\
How to configure and deploy an LDAP configuration file for external registration
Install the Java RSSE external registration example on BIRT iHub by performing the following tasks:
1 Using a source code editor, create an LDAP configuration file and copy or type the following code, substituting the values appropriate for the LDAP server installation:
<!--"-->
<Config>
<!-- Name of the LDAP server. -->
<Server>servername</Server>
<!-- Port number where the LDAP server listens. The
default port is 389. -->
<Port>389</Port>
<!-- LDAP distinguished name that the RSSE application uses for a query operation to the LDAP server. The Open Security application uses this account to validate users, roles, ACLs, and other user information. Account with READ privilege is sufficient. -->
<QueryAccount>uid=admin, ou=Administrators,
ou=TopologyManagement, o=NetscapeRoot</QueryAccount>
<!-- Password for the LDAP account specified by the QueryAccount parameter. -->
<QueryPassword>actuate</QueryPassword>
<!-- LDAP distinguished name that the RSSE application uses to locate the LDAP user object, including attributes for the organizational unit, ou, and domain components, dc. -->
<UserBaseDN>ou=AcUsers,dc=actuate,dc=com</UserBaseDN>
<!-- Name of LDAP object class that the Actuate open security application uses to find Actuate user names. -->
<UserObject>inetorgperson</UserObject>
<!-- Actuate role attribute that indicates that an LDAP user object can perform Encyclopedia volume administration. -->
<AdminRole>AcAdmin</AdminRole>
<!-- LDAP role object name that maps to the Encyclopedia volume Operator role. -->
<OperatorRole>AcAdmin</OperatorRole>
<!-- LDAP role object that maps to the All role in the Encyclopedia volume. -->
<AllRole>All</AllRole>
<!-- LDAP distinguished name that the RSSE application uses to locate the LDAP role object. -->
<RoleBaseDN>ou=AcRoles,dc=actuate, dc=com</RoleBaseDN>
<!-- LDAP object class that the Actuate open security application uses to find Actuate role names. -->
<RoleObject>groupofuniquenames</RoleObject>
<!-- LDAP distinguished name that the RSSE application uses to locate the LDAP Actuate notification group object. GroupBaseDN can be the same as the role DN, if Group information is not separately maintained. -->
<GroupBaseDN>ou=groups,dc=actuate, dc=com</GroupBaseDN>
<!-- LDAP object class that the Actuate open security
application uses to find Actuate notification group
names. -->
<GroupObject>groupofuniquenames</GroupObject>
<!-- Name of the LDAP group used for notifications of all job requests made in the iHub. The base DN is obtained from GroupBaseDN. -->
<GroupToNotify>specialGroup</GroupToNotify>
<!-- LDAP attribute used to retrieve the EmailAddress property of the user. No default value. -->
<EmailAddressAttr>mail</EmailAddressAttr>
<!-- LDAP attribute used to retrieve the license option property of the user. No default value. -->
<LicenseOptionsAttr>actuatelicenseoptions
</LicenseOptionsAttr>
<!-- LDAP attribute used to retrieve the HomeFolder property of the user. No default value. -->
<HomeFolderAttr>actuateHomeFolder</HomeFolderAttr>
<!-- LDAP attribute used to retrieve the AttachReportInEmail property of the user. --> <AttachReportInEmailAttr>actuateEmailForm
</AttachReportInEmailAttr>
<!-- Permitted values are "included" or "linked". The default value is "linked". -->
<AttachReportInEmailDefault>linked
</AttachReportInEmailDefault>
<!-- LDAP attribute used to retrieve the email preferences, SendEmailForSuccess and SendEmailForFailure properties of the user. For some object classes such as inetorgperson, an e‑mail attribute exists in the standard LDAP schema. -->
<SendEmailAttr>actuateEmailWhen</SendEmailAttr>
<!-- Permitted values are "never", "always", "failures", or "successes". -->
<SendEmailDefault>never</SendEmailDefault>
<!-- LDAP attribute used to retrieve the notification preferences, SendNoticeForSuccess and SendNoticeForFailure properties of the user. -->
<SendNoticeAttr>actuateFolderWhen</SendNoticeAttr>
<!-- Permitted values are "never", "always", "failures", "successes". -->
<SendNoticeDefault>always</SendNoticeDefault>
<!-- LDAP attribute used to retrieve the SuccessNoticeExpiration property of the user. The default value causes BIRT iHub to delete notices according to volume settings.-->
<SuccessNoticeExpirationAttr>
actuateSuccessNoticeExpiration
</SuccessNoticeExpirationAttr>
<!-- Value to use for SuccessNoticeExpirationAttr when LDAP does not contain a value for that attribute. The value is the number of minutes. The default value of 0 (zero) causes BIRT iHub to delete notices according to volume settings. A value of -1 means that BIRT iHub keeps notices indefinitely. -->
<SuccessNoticeExpirationDefault>0
</SuccessNoticeExpirationDefault>
<!-- LDAP attribute used to retrieve the FailureNoticeExpiration property of the user. The default value causes BIRT iHub to delete notices according to volume settings. -->
<FailureNoticeExpirationAttr>actuateFailNoticeExpiration
</FailureNoticeExpirationAttr>
<!-- Value to use for FailureNoticeExpirationDefault when LDAP does not contain a value for that attribute. The value is the number of minutes. The default value of 0 (zero) causes BIRT iHub to delete notices according to volume settings. A value of -1 means that BIRT iHub keeps notices indefinitely. -->
<FailureNoticeExpirationDefault>0
</FailureNoticeExpirationDefault>
<!-- LDAP attribute used to retrieve the privilege template for a user. Value is a comma-separated list of user or role privileges. A user permission is a user name followed by "=" and a string of 0 (zero) or more permission characters. A role permission is a role name followed by a "~" and a string of permission characters.
Permissible characters and their meanings are:
"r" = read
"w" = write
"e" = execute
"d" = delete
"v" = visible
"s" = secure read (page level read)
"g" = grant
Examples: bob=rwed, viewing only~rv -->
<PrivilegeTemplateAttr>actuateDefaultPriv
</PrivilegeTemplateAttr>
<!-- Value to use for PrivilegeTemplateAttr when LDAP does
not contain a value for that attribute. -->
<PrivilegeTemplateDefault/>
<!-- LDAP attribute used to retrieve the MaxJobPriority property of the user. The default value is 500. The permissible range is 0-1000. -->
<MaxJobPriorityAttr>actuateMaxPriority
</MaxJobPriorityAttr>
<!-- Value to use for MaxJobPriority when LDAP does not contain a value for that attribute. Default is 500. -->
<MaxJobPriorityDefault>500</MaxJobPriorityDefault>
<!-- LDAP attribute used to retrieve the ViewPreference property of the user. -->
<ViewPreferenceAttr>actuateViewingPref
</ViewPreferenceAttr>
<!-- Value to use for ViewPreferenceAttr when LDAP does not contain a value for that attribute. Permissible values are "default" and "dhtml".-->
<ViewPreferenceDefault>default</ViewPreferenceDefault> <!-- LDAP attribute used to retrieve the channel subscription list of the user. The values are specified as a comma-separated list. -->
<ChannelSubscriptionListAttr>actuateChannelList
</ChannelSubscriptionListAttr>
<!-- Value to use for ChannelSubscriptionListAttr when LDAP does not contain a value for that attribute. The value is a comma-separated lists of channel names or is empty. -->
<ChannelSubscriptionListDefault/>
<ConnectionPropertyList>
<ConnectionProperty>
<Name>username</Name>
<Value>testUser</Value>
</ConnectionProperty>
<ConnectionProperty>
<Name>password</Name>
<Value>mypassword</Value>
</ConnectionProperty>
</ConnectionPropertyList>
<!-- LDAP attributes used when externalizing ConnectionPropertyList, containing username and password. Typically used when implementing pass-through security. Do not include the ConnectionPropertyList if not externalizing these properties. -->
<ConnectionPropertyList>
<ConnectionProperty>
<Name>username</Name>
<Value>testUser</Value>
</ConnectionProperty>
<ConnectionProperty>
<Name>password</Name>
<Value>mypassword</Value>
</ConnectionProperty>
</ConnectionPropertyList>
</Config>
2 Save the file to the following location, naming the file, ldapconfig_$volumeName.xml, changing $volumeName to the Encyclopedia volume name:
$SERVER_HOME\etc\
How to configure external user registration
To use a Java RSSE application that utilizes LDAP for external user registration, the system administrator must enable an Open Security web service in System Console—User Management—RSSE Soap Service Settings, then restart the system. Also, configure an LDAP server database to contain the Encyclopedia volume’s user information. For more information about configuring the LDAP server database, see the LDAP server documentation.
How to configure an RSSE SOAP Service
To configure an RSSE SOAP service that uses an RSSE web service application, perform the following tasks:
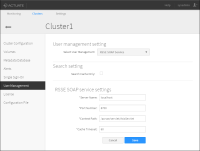
1 In System Console, choose Clusters, then choose Edit for an existing cluster.
2 Choose User Management.
3 In User Management Setting—Select User Management, choose RSSE SOAP Service.
4 In RSSE SOAP service settings, configure the following properties for the RSSE SOAP Service, as shown in
Figure 29‑3:

RSSE SOAP service settings
Contains the following properties:

Server Name
Machine name of the server that runs the RSSE web service.

Port Number
Port number for the RSSE web service.

Context Path
Specifies the location of the RSSE web service for iHub to use when sending messages to the web service. The default path is /acrsse/servlet/AxisServlet.

Cache Timeout
Number of minutes before BIRT iHub deletes cached data
Figure 29‑3 Configuring RSSE SOAP service settings